ERR_SSL_VERSION_OR_CIPHER_MISMATCH
After you add a new domain to Cloudflare, your visitors’ browsers might display ERR_SSL_VERSION_OR_CIPHER_MISMATCH (Chrome) or SSL_ERROR_NO_CYPHER_OVERLAP (Firefox) errors.
This error occurs when your domain or subdomain is not covered by an SSL/TLS certificate, which is usually caused by:
- A delay in certificate activation.
- An unproxied domain or subdomain DNS record.
- An expired Custom certificate.
- A multi-level subdomain (
test.dev.example.com).
Decision tree
Certificate activation
For domains on a full setup1, your domain should automatically receive its Universal SSL certificate within 15 minutes to 24 hours of domain activation2.
This certificate will cover your zone apex (example.com) and all first-level subdomains (subdomain.example.com), as long as your domain or subdomains have proxied DNS records within Cloudflare DNS.
Potential issues
If your visitors experience ERR_SSL_VERSION_OR_CIPHER_MISMATCH (Chrome) or SSL_ERROR_NO_CYPHER_OVERLAP (Firefox), check the status of your Universal certificate:
- Log into the Cloudflare dashboard.
- Choose your account and domain.
- Go to SSL > Edge Certificates.
- Find the certificate with the Type of Universal.
- Make sure the Status is Active.
If the Status is anything other than Active, you can either wait a bit longer for certificate activation or take immediate action.
Solutions
If you need to immediately resolve this error, temporarily pause Cloudflare.
Since Universal certificates can take up to 24 hours to be issued, wait and monitor the certificate’s status. Once your certificate becomes Active, unpause Cloudflare using whichever method you used previously.
If your certificate is still not Active after 24 hours, try the various troubleshooting steps used to resolve timeout issues. If these methods are successful (and your certificate becomes Active), unpause Cloudflare using whichever method you used previously.
Proxied DNS records
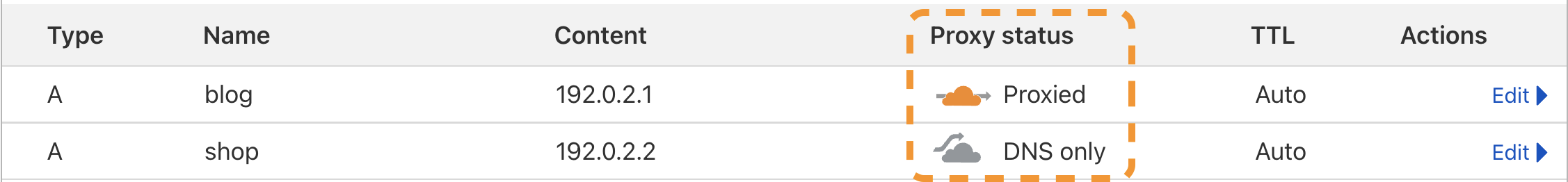
Cloudflare Universal and Advanced certificates only cover the domains and subdomains you have proxied through Cloudflare.
If the Proxy status of A, AAAA, or CNAME records for a hostname are DNS-only, you will need to change it to Proxied.
Certificate expiration
If you have a Custom certificate and visitors experience ERR_SSL_VERSION_OR_CIPHER_MISMATCH (Chrome) or SSL_ERROR_NO_CYPHER_OVERLAP (Firefox), check its status to make sure it is not expired.
If it is expired, upload a replacement certificate.
Multi-level subdomains
By default, Cloudflare Universal SSL certificates only cover your apex domain and one level of subdomain.
| Hostname | Covered by Universal certificate? |
|---|---|
example.com | Yes |
www.example.com | Yes |
docs.example.com | Yes |
dev.docs.example.com | No |
test.dev.api.example.com | No |
This means that you might experience ERR_SSL_VERSION_OR_CIPHER_MISMATCH (Chrome) or SSL_ERROR_NO_CYPHER_OVERLAP (Firefox) on multi-level subdomains.
To prevent insecure connections on a multi-level subdomain, do one of the following:
- Enable Total TLS, which automatically issues individual certificates to your proxied hostnames not covered by a Universal certificate.
- Order an Advanced Certificate covering the subdomain.
- Upload a Custom Certificate covering the subdomain.
If none of these solutions work, you could also remove the multi-level subdomain.