Find an appropriate rate limit
The Rate limit analysis tab in Security Analytics displays data on the request rate for traffic matching the selected filters and time period. Use this tab to determine the most appropriate rate limit for incoming traffic matching the applied filters.
User interface overview
The Rate limit analysis tab is available at the zone level in Security > Analytics.
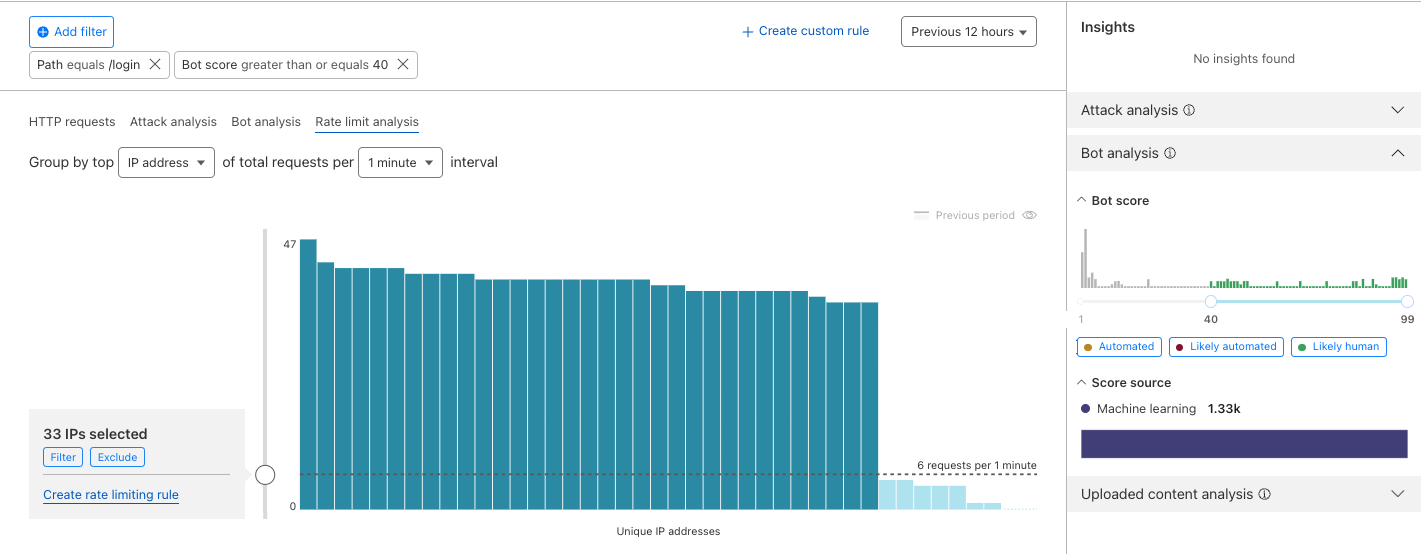
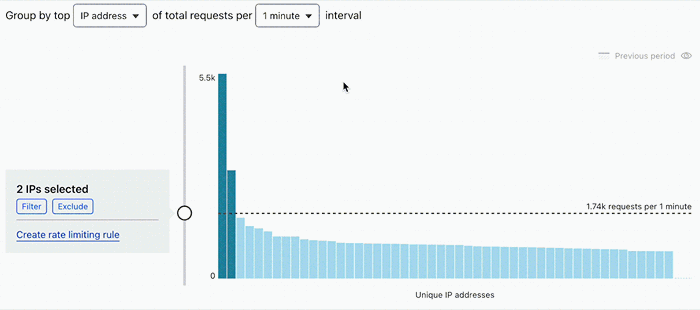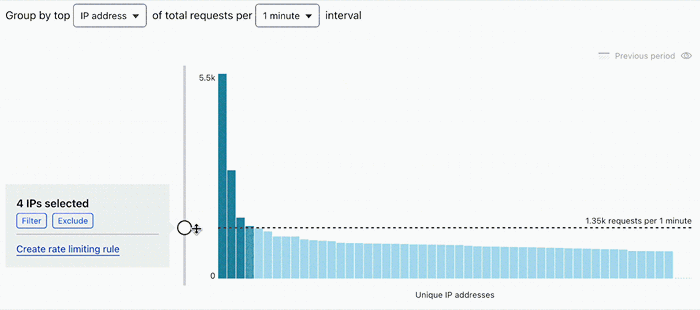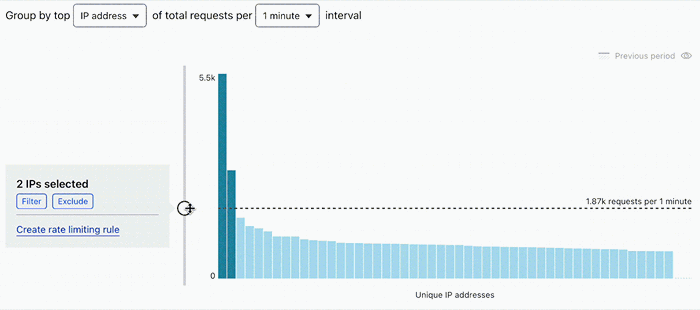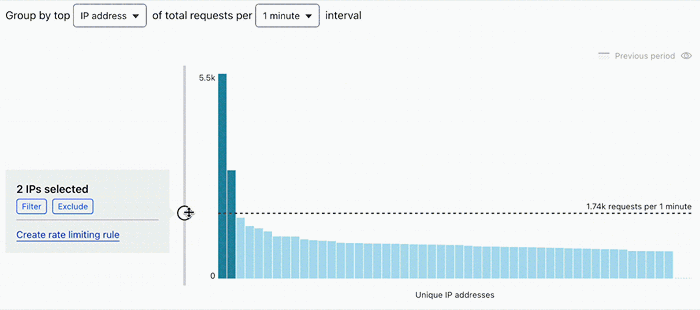
The main chart displays the distribution of request rates for the top 50 unique clients observed during the selected time interval (for example, 1 minute) in descending order. You can group the request rates by the following unique request properties:
- IP address
- JA3 fingerprint (only available to customers with Bot Management)
- IP address and JA3 fingerprint (only available to customers with Bot Management)
Determine an appropriate rate limit
1. Define the scope
Log in to the Cloudflare dashboard, and select your account and zone.
Go to Security > Analytics.
In the HTTP requests tab, select a specific time period:
- To look at the regular rate distribution, specify a period with non-peak traffic.
- To analyze the rate of offending visitors/bots, select a period corresponding to an attack.
Apply filters to analyze a particular situation in your application where you want to apply rate limiting (for example, filter by
/loginURL path).(Optional) To focus on non-automated/human traffic, use the bot score quick filter in the sidebar.
2. Find the rate
Choose the request properties (JA3, IP, or both) and the duration (1 min, 5 mins, or 1 hour) for your rate limit rule. The request properties you select will be used as rate limiting rule characteristics.
Use the slider in the chart to move the horizontal line defining the rate limit. While you move the slider up and down, check the impact of defining a rate limiting rule with the selected limit on the displayed traffic.
3. Validate your rate
Repeat the rate selection process described in the previous section, but selecting a portion of traffic where you know there was an attack or traffic peak. The rate you have chosen should block the outlier traffic during the attack and allow traffic during regular periods.
(Optional) Check the sampled logs to verify the fingerprints and filters you selected.
4. Create a rate limiting rule
Select Create rate limit rule to go to the rate limiting creation page with your filters, characteristics, and selected rate limit pre-populated.
Select the rule action. Depending on your needs, you can set the rule to log, challenge, or block requests exceeding the selected threshold.
It is recommended that you first deploy the rule with the Log action to validate the threshold, and change the action later to block or challenge incoming requests when you are confident about the rule behavior.
To save and deploy your rate limiting rule, select Deploy. If you are not ready to deploy your rule, select Save as Draft.